
QNAP has warned customers today to secure Internet-exposed network-attached storage (NAS) devices immediately from ongoing ransomware and brute-force attacks.
"QNAP urges all QNAP NAS users to follow the security setting instructions below to ensure the security of QNAP networking devices," the Taiwanese NAS maker said in a press release issued today.
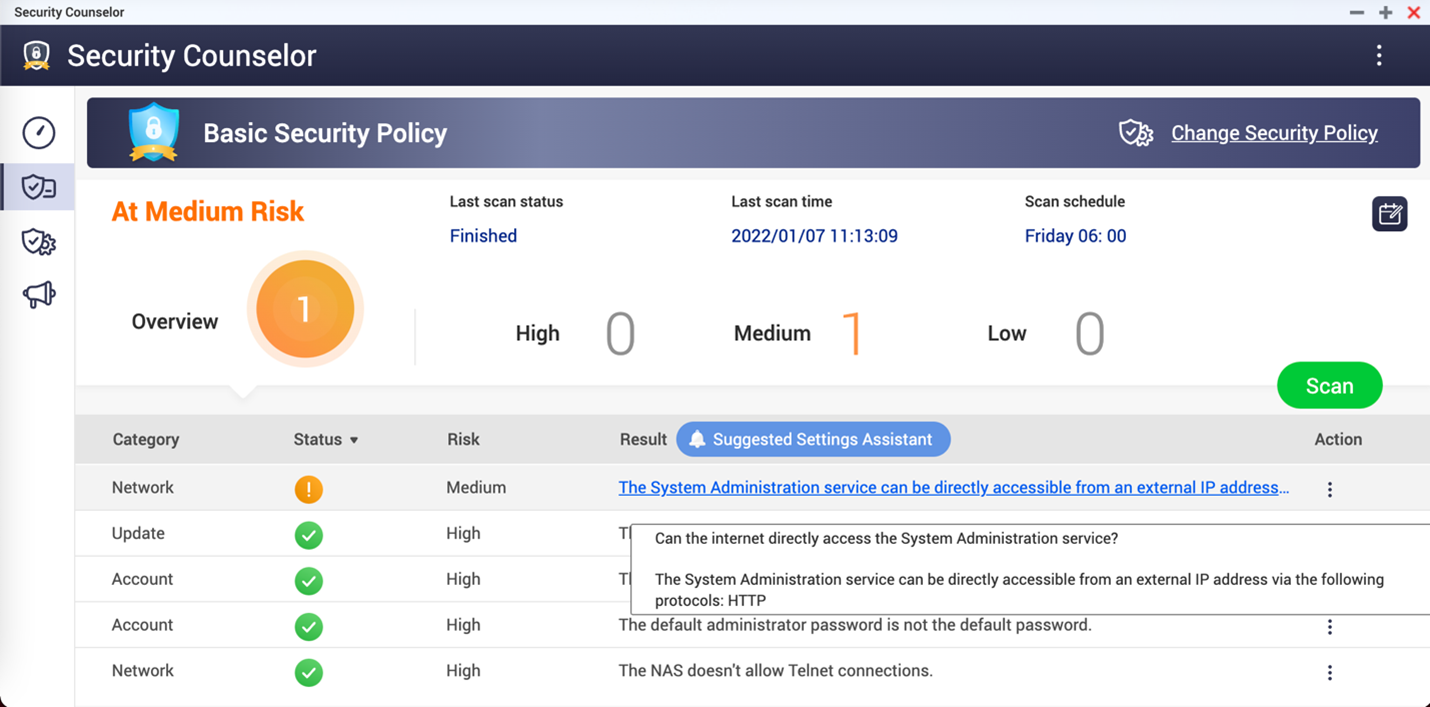
The company warned users to check if their NAS is accessible over the internet by opening the Security Counselor, a built-in security portal for QNAP NAS devices.
"Your NAS is exposed to the Internet and at high risk if there shows 'The System Administration service can be directly accessible from an external IP address via the following protocols: HTTP' on the dashboard."
QNAP advises customers who have NAS devices exposed to Internet access to take the following actions to defend them from attacks:
- Disable the Port Forwarding function of the router: Go to the management interface of your router, check the Virtual Server, NAT, or Port Forwarding settings, and disable the port forwarding setting of NAS management service port (port 8080 and 433 by default).
- Disable the UPnP function of the QNAP NAS: Go to myQNAPcloud on the QTS menu, click the "Auto Router Configuration," and unselect "Enable UPnP Port forwarding."
The NAS maker also provides detailed step-by-step procedures on how to toggle off SSH and Telnet connections and change the system port number, change device passwords and enable IP and account access protection.
Warning follows a surge of ransomware attacks
While the company did not share any other details on these active attacks, BleepingComputer reported on QNAP customers saying their systems were targeted with eCh0raix ransomware (also known as QNAPCrypt).
These incidents follow an increase in activity right before Christmas and are using an unknown attack vector.
However, some of the users' reports seen by BleepingComputers link successful ransomware attacks to improperly secured Internet-exposed devices. Others have also claimed that the attackers exploited an unspecified QNAP Photo Station vulnerability.
BleepingComputer has seen ech0raix ransom demands ranging from $1,200 to $3,000 worth of bitcoins during these recent attacks. Some of them were paid because the victims didn't have a backup of the encrypted files
QNAP devices were previously targeted by threat actors using eCh0raix ransomware in June 2019 and June 2020, with the NAS maker also alerting users of another series of another surge of eCh0raix attacks targeting devices with weak passwords in May 2021.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now